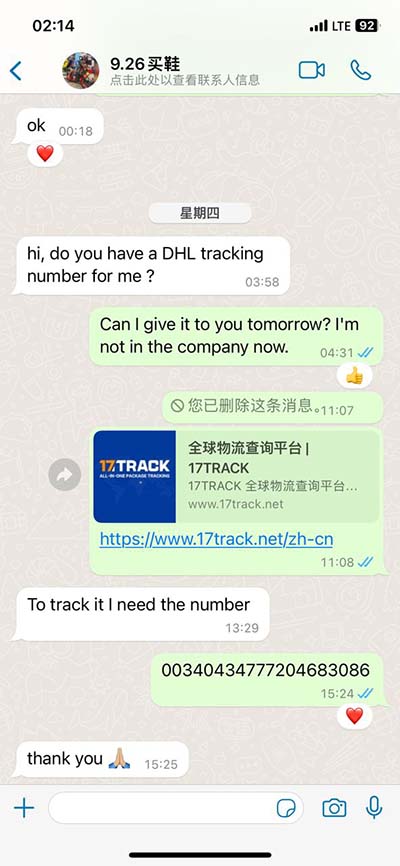
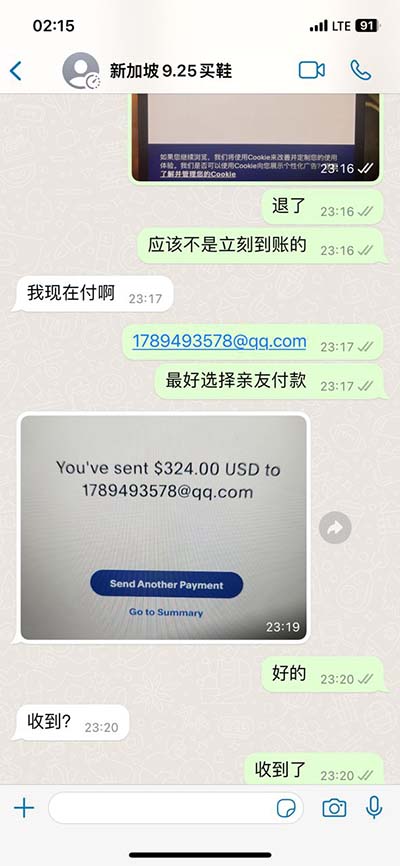
hacker hermes | hermes birkin so black hacker hermes In mid-August 2018, a modified version of Hermes, dubbed Ryuk, started appearing in a public malware repository. Ryuk was tailored to target enterprise environments and some . Advances in Vision-Based Lane Detection: Algorithms, Integration, Assessment, and Perspectives on ACP-Based Parallel Vision. Y Xing, C Lv, L Chen, H Wang, H Wang, D Cao, E Velenis, FY Wang. IEEE/CAA Journal of Automatica Sinica 5 (3), 645-661. , .
0 · original birkin bags by hermes
1 · most expensive hermes bag ever
2 · hermes most expensive item
3 · hermes hac price
4 · hermes hac a dos price
5 · hermes hac 50 bag
6 · hermes hac 40 price
7 · hermes birkin so black
This bundle includes all of the vocab and grammar review handouts that I have created for Chapters 1-6 of Bien Dit 2. The first page of each handout has all a list of the vocabulary from the chapter, in French and English.

> Hermes uses Golang for the backend and Ember.js for the front end. It uses a PostgreSQL database for storage and Algolia to power its search capabilities. It also leverages . In mid-August 2018, a modified version of Hermes, dubbed Ryuk, started appearing in a public malware repository. Ryuk was tailored to target enterprise environments and some .To begin, start typing on your keyboard and your hacker code will immediately appear! You can also enter full screen in your browser. To enhance your experience, press Shift or Alt (or .
The key is that Hermes is optimized for a totally different environment and workload - RN apps from disk on slow Android devices vs. websites downloaded on desktop computers. The fact ."Static Hermes is the the next major version of Hermes, still under active development. It enables optional ahead-of-time native compilation of soundly typed JavaScript, using TypeScript or . Evidence suggests the infamous Lazarus Group, a hacking crew believed to be operating out of North Korea, is behind the recent hack on the Far Eastern International Bank .
The HAC is one of the oldest bags created by Hermès. With its own unique and particular style, it was originally designed to carry riding equipment such as saddles and boots. .This community-curated security page documents any known process for reporting a security vulnerability to Hermès, often referred to as vulnerability disclosure (ISO 29147), a responsible .
Today, after GData security researcher Karsten Hahn discovered a new ransomware called Hermes, Fabian decided to use it as the sample for his first live streaming . Explore easy IKEA Hemnes hacks to customize your furniture. Find DIY tips for painting, hardware changes, and more for a unique home style.About. Hermes is HackerOne's homegrown test impact analysis framework used for selective test running and dependency analysis. Resources
original birkin bags by hermes
Hacker News new | past | comments | ask | show | jobs | submit: login: Hermes: An open-source document management system (hashicorp.com) . This Hermes seems nice and being open source is a great thing but it's still in alpha, do not support custom file types and very Google oriented.Hermes (and all gods who represent the trickster archetype) was the first hacker. The one who use his intelligence to archieve things, the one who outsmart u, the one who pursue knowledge, the thief, the society student. Hermes: A Text-to-SQL Solution at Swiggy - Hacker News . Search:The Hacker News is the most trusted and popular cybersecurity publication for information security professionals seeking breaking news, actionable insights and analysis. #1 Trusted Cybersecurity News Platform.
Inscrivez-vous a Hacker Professionnel - Hacking, Piratage Informatique, Investigation, Forensic, NCHO YAO - NYS Africa Abidjan, Cote d'Ivoire. Expert2425; Appelez-nous. Appelez-nous. LOUA Jean Hermes #2256 Crypto-Consultant. Félicitations à LOUA . Emily, of the Jones Design Co, turned an unused room above the garage into 'an inviting, inspiring place to work and create', and carried out a clever IKEA Hemnes hack to make the statement desk. 'After lots and lots of research on desk options, I finally settled on a diy version – or as they say, an IKEA hack,' says Emily.'
Hacker Typer. Minimize or close all windows and start pressing random buttons on your keyboard to simulate that you're writing program. The hacker typer will add more than one character at once to the screen to make your writing look faster. Open the "Remote Connection" program to simulating that you're hacking a top secret governmet server.
One final ting to take note of is that this hack only works on Apple Watches with watchOS 3.0-3.1.1 installed on them at this point in time. This is because you need an iPhone jailbroken on iOS 10.0-10.2 with Yalu to use it. The watchOS 3.0 release was made for iOS 10, the watchOS 3.1 release was made for iOS 10.1, and the watchOS 3.1.1 release .Gary McKinnon (Glasgow, 10 de fevereiro de 1966) é um Hacker escocês [1] acusado pelos Estados Unidos de perpetrar o "maior ataque de todos os tempos a computadores militares". [2] Depois de várias audiências realizadas em julho de 2006 no Reino Unido, foi decidido que ele deveria ser extraditado para os Estados Unidos.Seus advogados apelaram contra esta . «La Tabla Esmeralda» de Hermes Trismegisto. Crédito: «Amphitheatrvm sapientiae aeternae, solivs verae«, 1609, por Heinrich Khunrath (1560-1605) / Dominio Público. En ‘La Tabla Esmeralda‘, un libro que fue traducido al inglés por nada más y nada menos que Isaac Newton, nos explica que todo lo que existe y lo que no existe forma parte del TODO.
Want to become an ethical hacker? We’ve found the 19 best hacking tools in 2024, inc. networking hacking, password cracking, and vulnerability assessment. #picotin #hermeshaul #whatsinmybag Hi everyone, a bit of a long video today. I have a mini Hermes haul and a six month review of my Picotin MM. I show you th.
The FBI and the U.S. Cybersecurity & Infrastructure Security Agency (CISA) have disclosed that Chinese hackers breached commercial telecommunication service providers in the United States. > Hermes uses Golang for the backend and Ember.js for the front end. It uses a PostgreSQL database for storage and Algolia to power its search capabilities. It also leverages several Google Workspace services for creating and modifying documents, sending email, etc.
most expensive hermes bag ever
In mid-August 2018, a modified version of Hermes, dubbed Ryuk, started appearing in a public malware repository. Ryuk was tailored to target enterprise environments and some of the modifications include removing anti-analysis checks.To begin, start typing on your keyboard and your hacker code will immediately appear! You can also enter full screen in your browser. To enhance your experience, press Shift or Alt (or Option for Mac) three times.The key is that Hermes is optimized for a totally different environment and workload - RN apps from disk on slow Android devices vs. websites downloaded on desktop computers. The fact that Hermes is architected for RN from the beginning is key."Static Hermes is the the next major version of Hermes, still under active development. It enables optional ahead-of-time native compilation of soundly typed JavaScript, using TypeScript or Flow type annotations."
Evidence suggests the infamous Lazarus Group, a hacking crew believed to be operating out of North Korea, is behind the recent hack on the Far Eastern International Bank (FEIB) in Taiwan. The HAC is one of the oldest bags created by Hermès. With its own unique and particular style, it was originally designed to carry riding equipment such as saddles and boots. Emile-Maurice Hermès – the grandson of the company founder, Thierry Hermès – .This community-curated security page documents any known process for reporting a security vulnerability to Hermès, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.

Today, after GData security researcher Karsten Hahn discovered a new ransomware called Hermes, Fabian decided to use it as the sample for his first live streaming session. The best part of it is.
cartier gold necklaces
cartier glasses buff
Challenge to win medals by defeating computer! You will be rewarded new board style and pieces design by collecting medals. The Chess Lv.100 is the most downloaded chess app for Microsoft Store! (Free app) Introduced online game feature!!
hacker hermes|hermes birkin so black